Digital security is no longer just a concern for large enterprises or tech-heavy organizations. As more personal, professional, and financial activities move online, cyber threats have become a daily reality for businesses and individuals alike. From phishing attacks and ransomware to data breaches and identity theft, the risks continue to evolve.
This is where advanced cybersecurity tools play a critical role. Unlike basic security solutions, modern tools are designed to detect, analyze, and respond to threats in real time—often before users even realize an attack is underway. Understanding how these tools work can help organizations and individuals make smarter security decisions.
The Shift From Basic Protection to Advanced Security
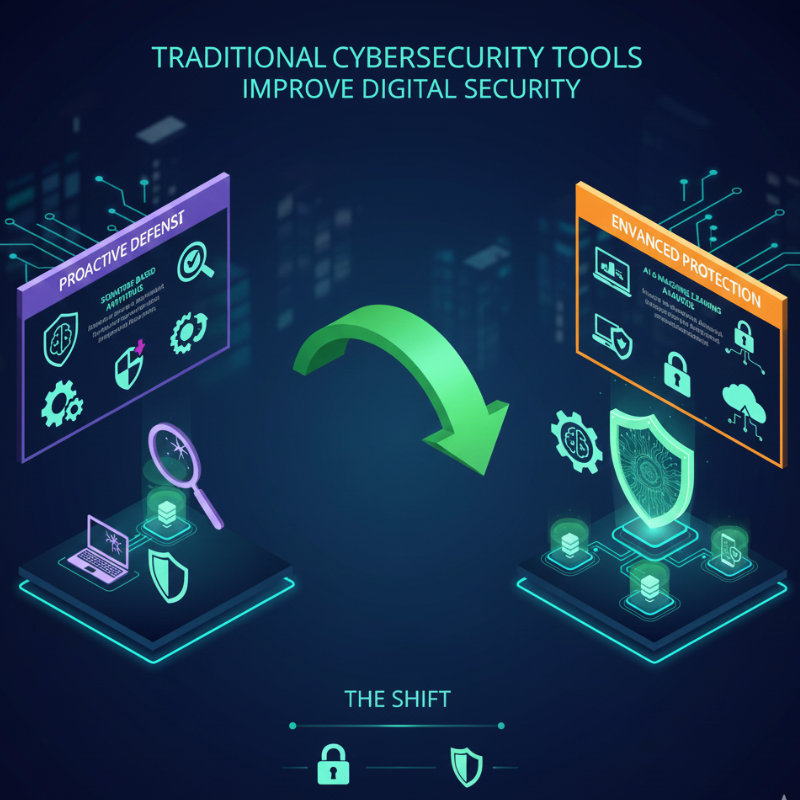
Traditional cybersecurity relied heavily on signature-based antivirus software. While effective in the past, this approach struggles against modern threats that constantly change their behavior.
Advanced cybersecurity tools use a combination of artificial intelligence, machine learning, behavioral analysis, and real-time monitoring. Instead of reacting to known threats alone, they identify suspicious patterns and anomalies, allowing systems to respond proactively.
This shift has transformed cybersecurity from a reactive measure into a predictive and adaptive defense system.
Real-Time Threat Detection and Response

One of the biggest advantages of advanced cybersecurity tools is their ability to detect threats in real time. These tools continuously monitor networks, devices, and user behavior to spot unusual activity.
If an attacker attempts to gain unauthorized access, deploy malware, or exploit a vulnerability, advanced systems can immediately flag the threat and trigger an automated response. This may include isolating affected devices, blocking malicious traffic, or alerting administrators before damage occurs.
Speed matters in cybersecurity, and real-time response significantly reduces potential harm.
AI and Machine Learning in Cyber Defense

Artificial intelligence has become a cornerstone of modern cybersecurity. AI-driven tools analyze vast amounts of data to identify patterns that would be impossible for humans to detect manually.
Machine learning models improve over time, learning from previous attacks and adapting to new threat techniques. This allows cybersecurity tools to recognize zero-day attacks—threats that have not yet been documented or catalogued.
By continuously learning, these systems stay ahead of attackers rather than simply reacting to known risks.
Improved Protection Against Phishing and Social Engineering
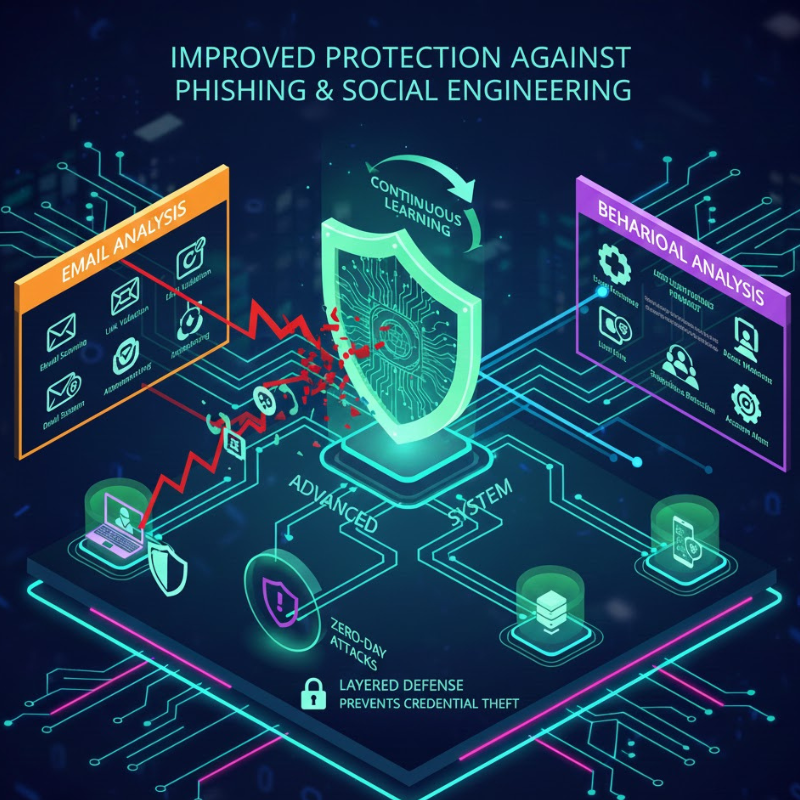
Phishing remains one of the most effective attack methods, largely because it targets human behavior rather than technical vulnerabilities. Advanced cybersecurity tools combat this by analyzing email content, sender reputation, links, and attachments in real time.
Some tools also use behavioral analysis to identify unusual login attempts or suspicious account activity. This layered approach reduces the likelihood of successful phishing attacks and helps prevent credential theft.
Enhanced Network Visibility and Control
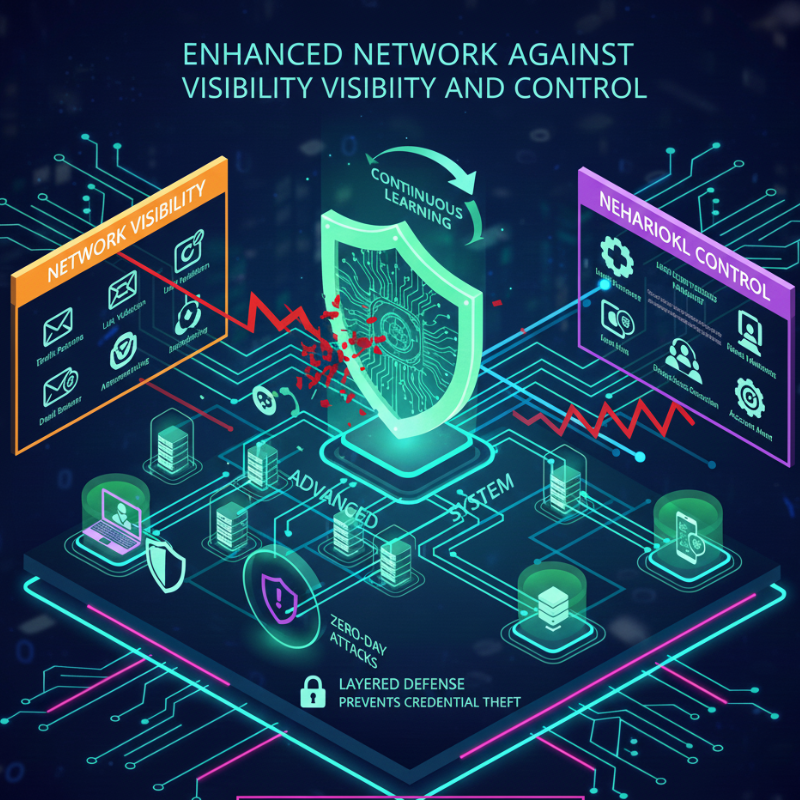
Advanced cybersecurity solutions provide deeper visibility into network activity. Instead of simply blocking known threats, they offer detailed insights into traffic patterns, device behavior, and user access levels.
This visibility allows organizations to identify weak points, enforce access controls, and detect lateral movement within networks—where attackers move quietly after gaining initial access.
Better visibility leads to better control, which is essential for maintaining long-term digital security.
Automation That Reduces Human Error
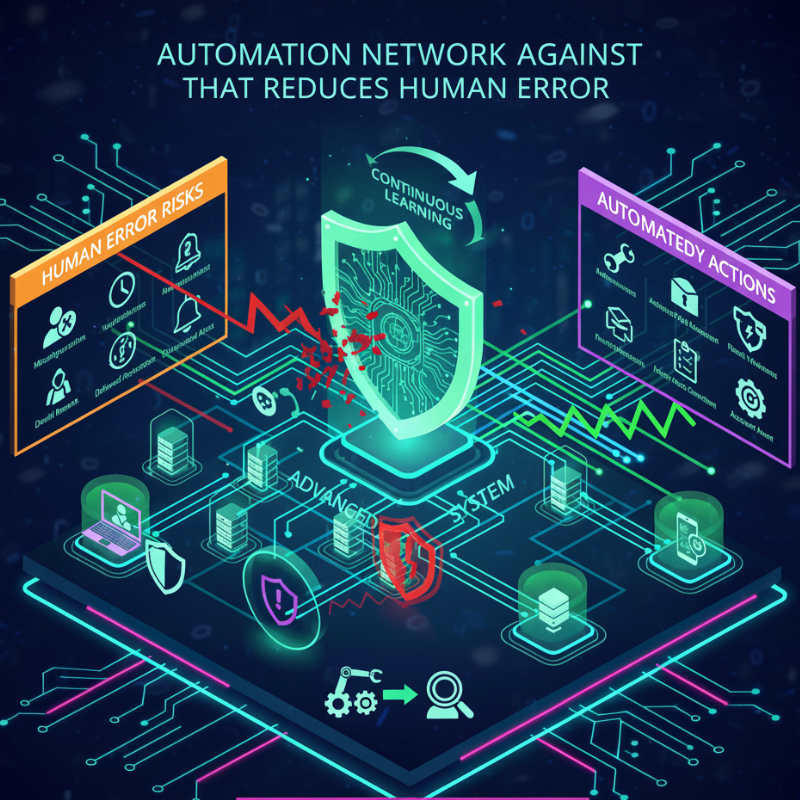
Human error is one of the leading causes of security breaches. Misconfigurations, delayed responses, or overlooked alerts can all create opportunities for attackers.
Advanced cybersecurity tools use automation to minimize these risks. Automated patch management, threat containment, and response workflows ensure that security actions are taken quickly and consistently.
Automation doesn’t replace human oversight—it enhances it by handling repetitive tasks and allowing security teams to focus on strategic decisions.
Cloud and Remote Work Security
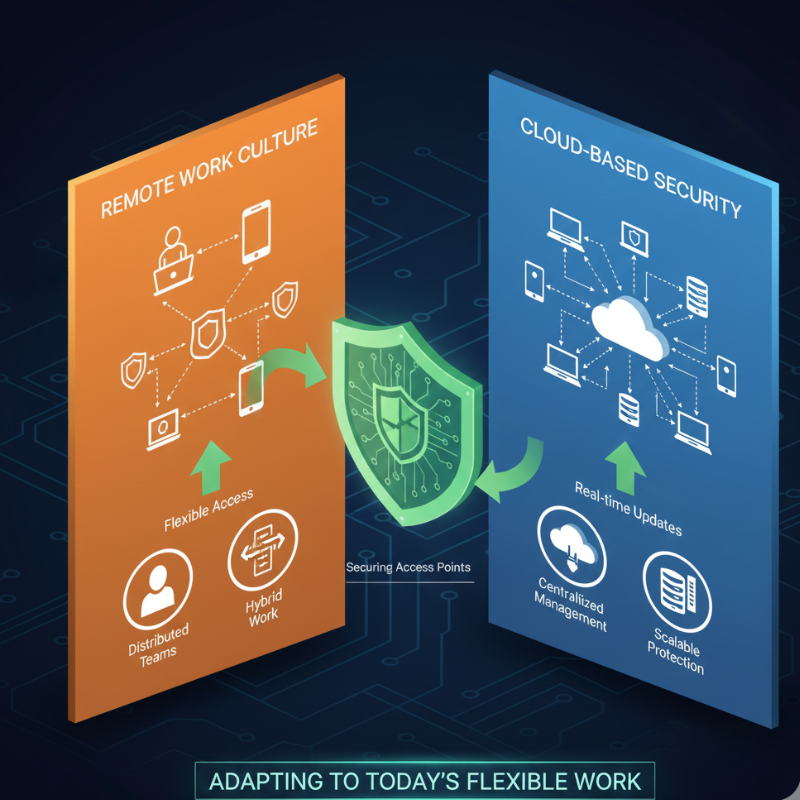
With the rise of cloud computing and remote work, traditional perimeter-based security models are no longer sufficient. Advanced cybersecurity tools are designed to protect users and data regardless of location.
Cloud-based security platforms offer centralized management, real-time updates, and scalable protection across devices and networks. This is especially valuable for businesses with distributed teams or hybrid work environments.
By securing access points rather than physical locations, modern tools adapt to today’s flexible work culture.
Compliance and Risk Management Benefits

Many industries are subject to strict data protection and cybersecurity regulations. Advanced cybersecurity tools often include features that support compliance with standards such as GDPR, ISO, or industry-specific frameworks.
Automated reporting, audit trails, and policy enforcement help organizations meet regulatory requirements while reducing administrative burden. This not only improves security but also minimizes legal and reputational risks.
Scalability for Growing Digital Needs

As digital operations expand, security needs grow more complex. Advanced cybersecurity tools are designed to scale alongside businesses, supporting additional users, devices, and services without major infrastructure changes.
Scalable solutions ensure that security remains consistent and effective, even as systems evolve.
Final Thoughts
Advanced cybersecurity tools have fundamentally changed how digital security is managed. By combining real-time monitoring, AI-driven analysis, automation, and cloud-based protection, these tools offer a smarter and more resilient defense against modern cyber threats.
At Your Tech Digest, we believe strong digital security starts with understanding the tools that protect it. Explore more insights, technology guides, and cybersecurity trends on our platform—and stay informed as the digital landscape continues to evolve.

























